Kemaren bg katoih minta perbaiki laptop Axioo yang sudah 2 kali install windows dan sudah 2 kali terkena Virus dan malware yang tidak bisa di detect oleh Antivirus ampuh yang saya miliki yaitu NOD32 Versi terbaru yang ada serial Number nya…:D, Saya merasa aneh dengan Laptop nya, kalau menggunakan Jaringan Internet LAN bisa koneksi tapi pas di PING menggunakan ping -t yahoo.com (si Windows Mengatakan : Cek name your spesifikasi) Dasar Dodol Neh Komputer itu nama udah benar malah dikatakan salah, kemudian Saya Coba Scan Menggunakan Trojan Removal, waktu scan emank Kedetetect salah satu File di Windows/System32/driver/ndis.sys< —Infected, Wah Aneh neh File, udah Kedetect dan Udah di Clean dan Quarantined Masih tetap Juga Aktif. AKhirnya Solusi Terakhir tanya sama Om Google,Dengan Mengetik infected repair ndis.sys, Ternyata solusinya menggunakan COMBOFIX. Berikut cara Penggunaan Combofix serta hasil Log saya ketika scan Komputer bg Katoih…yang membuat Akses internet anda lambat dan sering Time-out.
Using ComboFix
If you need help with malware removal, then please create a topic at one of the forums listed later in the guide and ask for help. Please note that each forum has different policies, so please be sure to read any pinned topics and rules for the particular forum about how you should go about receiving help. If a ComboFix log has been requested by a helper then please create one by following the instructions below.
The first thing you should do is print out this guide, as we will close all the open windows and programs, including your web browser, before starting the ComboFix program.
Next you should download ComboFix from one of the following URLs:
- BleepingComputer.com (Klick Kanan Kemudian-Klik Save Link As)
- ForoSpyware.com (Klick Kanan Kemudian-Klik Save Link As)
To download ComboFix, simply left-click on one of the links above and you will see a prompt similar to the figure below.
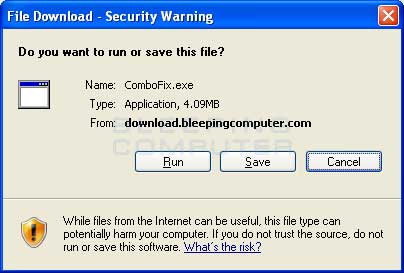
Download ComboFix Prompt
Click on the Save button, and when it asks you where to save it, make sure you save it directly to your Windows Desktop. An image showing this is below.
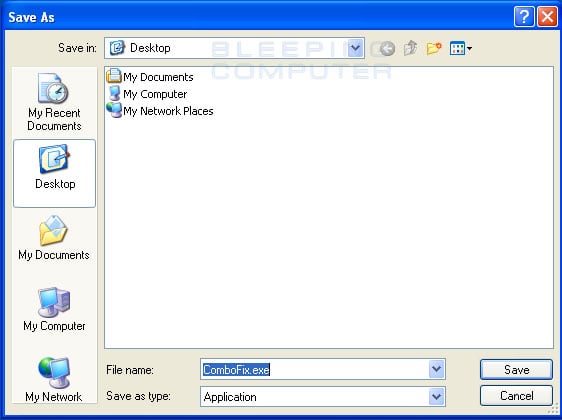
Downloading ComboFix to the Desktop
When you have the Save as screen configured to save ComboFix.exe to the Desktop, click on the Save button. ComboFix will now start downloading to your computer. If you are on a dialup, this may take a few minutes. When ComboFix has finished downloading you will now see an icon on your desktop similar to the one below.
![]()
ComboFix Icon
We are almost ready to start ComboFix, but before we do so, we need to take some preventative measures so that there are no conflicts with other programs when running ComboFix. At this point you should do the following:
- Close all open Windows including this one.
- Close or disable all running Antivirus, Antispyware, and Firewall programs as they may interfere with the proper running of ComboFix. Instructions on disabling these type of programs can be found in this topic.
Once these two steps have been completed, double-click on the ComboFix icon found on your desktop. Please note, that once you start ComboFix you should not click anywhere on the ComboFix window as it can cause the program to stall. In fact, when ComboFix is running, do not touch your computer at all. The scan could take a while, so please be patient.
Once you double-click on the icon, you may see a screen similar to the one below.
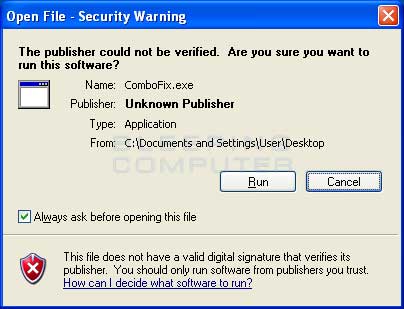
Windows Open File Security Warning
Windows is issuing this prompt because ComboFix does not have a digital signature. This is perfectly normal and safe and you can click on the Run button to continue. If you are using Windows Vista , and receive UAC prompt asking if you would like to continue running the program, you should press the Continue button.
, and receive UAC prompt asking if you would like to continue running the program, you should press the Continue button.
You will now see the first ComboFix screen as shown below.
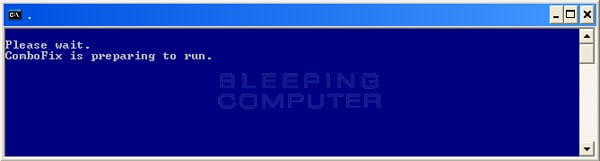
ComboFix is Preparing to Run
ComboFix is now preparing to run and when it has finished you will see a screen showing the authorized locations to download Combofix. On this screen please press the OK button and you will be shown the Disclaimer screen shown below.

ComboFix Disclaimer
If you do not agree to the disclaimer, then click on the No button to exit the program. Otherwise, to continue you should press the Yes button to continue. If you decided to continue, then ComboFix will create a System Restore point so that if any problems occur while using the program you can restore back to your previous configuration. When ComboFix has finished creating the restore point, it will then backup your Windows Registry as shown in the image below.
as shown in the image below.
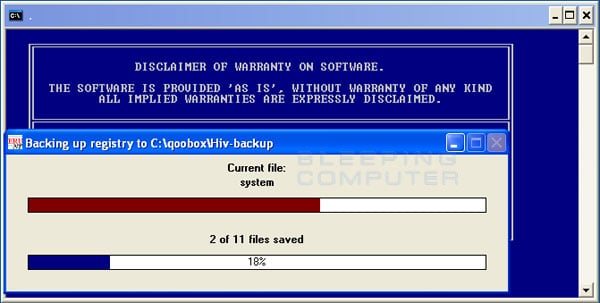
ComboFix is backing up the Windows Registry
Once the Windows Registry has finished being backed up, ComboFix will attempt to detect if you have the Windows Recovery Console installed. If you already have it installed, you can skip to this section and continue reading. Otherwise you will see the following message as shown below:
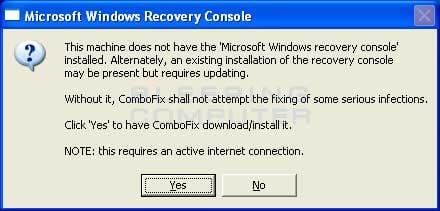
ComboFix Recovery Console
At the above message box, please click on the Yes button in order for ComboFix to continue. Please follow the steps and instructions given by ComboFix in order to finish the installation of the Recovery Console. Once it has finished installing, you will be presented with the screen shown below.
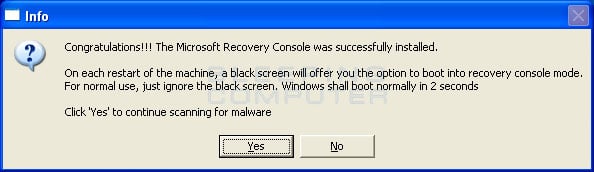
ComboFix Recovery Console Finished
You should now press the Yes button to continue. If at any time during the Recovery Console installation you receive a message stating that it failed to install, please allow ComboFix to continue with the scan of your computer. When it is done, and a log has been created, you can then perform the manual install of the Recovery Console using the steps found in the Manually installing the Windows Recovery Console section.
ComboFix will now disconnect your computer from the Internet, so do not be surprised or concerned if you receive any warnings stating that you are no longer on the Internet. When ComboFix has finished it will automatically restore your Internet connection.
ComboFix will now start scanning your computer for known infections. This procedure can take some time, so please be patient.
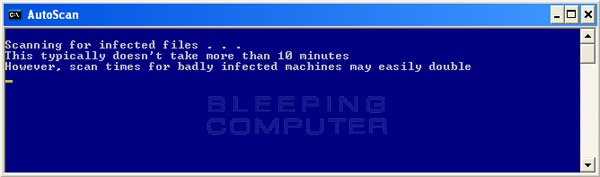
ComboFix is scanning the computer for infections
While the program is scanning your computer, it will change your clock format, so do not be concerned when you see this happen. When ComboFix is finished it will restore your clock settings to their previous settings. You will also see the text in the ComboFix window being updated as it goes through the various stages of its scan. An example of this can be seen below.
Stages of the ComboFix AutoScan
At the time of this writing there are a total of 50 stages as shown in the image below, so please be patient. The amount of stages will go up as time goes on, so if the amount of stages is different when you run it, please do not be concerned.
34th Stage of the ComboFix AutoScan
When ComboFix has finished running, you will see a screen stating that it is preparing the log report as shown below.
ComboFix is preparing the log report
This can take a while, so please be patient. If you see your Windows desktop disappear, do not worry. This is normal and ComboFix will restore your desktop before it is finished. Eventually you will see a new screen that states the program is almost finished and telling you the programs log file, or report, will be located at C:ComboFix.txt. This can be seen in the image below.
ComboFix is almost done!
When ComboFix has finished, it will automatically close the program and change your clock back to its original format. It will then display the log file automatically for you as shown below.
Berikut Log Hasil Scanning Laptop Bg Tusrisep Katoih…Terkena Rootkit.Trojan
ComboFix 10-06-14.01 – Tusrisep 06/15/2010 0:55.1.2 – x86
Microsoft Windows XP Professional 5.1.2600.2.1252.1.1033.18.958.683 [GMT 7:00]
Running from: c:documents and settingsTusrisepMy DocumentsHAJAR BLEHComboFix.exe
Command switches used :: c:documents and settingsTusrisepMy DocumentsHAJAR BLEHWindowsXP-KB310994-SP2-Pro-BootDisk-ENU.exe
AV: ESET NOD32 Antivirus 4.2 *On-access scanning disabled* (Updated) {E5E70D32-0101-4F12-8FB0-D96ACA4F34C0}
* Created a new restore point
* Resident AV is active
.
((((((((((((((((((((((((((((((((((((((( Other Deletions )))))))))))))))))))))))))))))))))))))))))))))))))
.
c:documents and settingsTusrisepsecupdat.dat
c:windowssystemBisonC07.dll
c:windowssystem3285.scr
c:windowssystem32asr_20128.exe
c:windowssystem32cbstuunm.dll.vir
c:windowssystem32driverszqahnull.sys
c:windowssystem32secupdat.dat
c:windowssystem32ubtzyvw.dll.vir
Infected copy of c:windowssystem32driversacpiec.sys was found and disinfected
Restored copy from – Kitty had a snack :p
c:windowssystem32driversndis.sys . . . is infected!!
.
((((((((((((((((((((((((((((((((((((((( Drivers/Services )))))))))))))))))))))))))))))))))))))))))))))))))
.
——-Legacy_ICF
——-Legacy_SSHNAS
——-Service_ICF
——-Service_SSHNAS
((((((((((((((((((((((((( Files Created from 2010-05-14 to 2010-06-14 )))))))))))))))))))))))))))))))
.
2010-06-14 15:34 . 2010-06-14 16:09 ——– d—–w- c:documents and settingsTusrisepLocal SettingsApplication DataTemp
2010-06-14 15:33 . 2010-06-14 16:11 ——– d—–w- c:documents and settingsTusrisepLocal SettingsApplication DataGoogle
2010-06-12 06:07 . 2010-02-27 13:46 3691384 —-a-w- c:documents and settingsTusrisepApplication DataSimply Super SoftwareTrojan Removerncj1D.exe
2010-06-11 16:58 . 2010-06-12 06:06 ——– d—–w- c:program filesTrojan Remover
2010-06-11 16:13 . 2010-06-11 16:12 212992 ——w- c:windowssystem32wmpsk2.exe
2010-06-01 06:20 . 2010-06-01 06:20 ——– d—–w- c:program filesTotal Video Converter
2010-05-26 10:08 . 2010-05-26 10:13 ——– d—–w- c:documents and settingsTusrisepLocal SettingsApplication DataPhotoJoy
2010-05-26 10:08 . 2010-05-26 10:08 ——– d—–w- c:program filesPhotoJoy
2010-05-26 10:08 . 2010-05-26 10:08 ——– d—–w- c:documents and settingsAll UsersApplication DataPhotoJoy
2010-05-19 11:58 . 2010-05-19 11:58 ——– d—–w- c:documents and settingsAll UsersApplication DataESET
.
(((((((((((((((((((((((((((((((((((((((( Find3M Report ))))))))))))))))))))))))))))))))))))))))))))))))))))
.
2010-06-14 16:57 . 2010-04-08 10:51 ——– d—–w- c:program filesSmadav
2010-06-14 14:24 . 2010-03-04 12:32 ——– d—–w- c:program filesMozilla Firefox 3.6 Beta 5
2010-06-12 06:07 . 2010-04-20 19:54 ——– d—a-w- c:documents and settingsAll UsersApplication DataTEMP
2010-06-12 06:06 . 2010-05-06 18:50 ——– d—–w- c:documents and settingsTusrisepApplication DataSimply Super Software
2010-06-12 06:02 . 2010-04-20 19:50 ——– d—–w- c:program filesAnti Trojan Elite
2010-06-11 15:56 . 2010-04-05 08:51 ——– d—–w- c:program filesIM2 Broadband 3.5G
2010-06-07 15:01 . 2010-03-24 12:34 ——– d—–w- c:program filesAsk.com
2010-06-01 06:25 . 2010-03-04 10:24 68848 —-a-w- c:documents and settingsTusrisepLocal SettingsApplication DataGDIPFONTCACHEV1.DAT
2010-05-19 11:58 . 2010-03-04 10:25 ——– d—–w- c:program filesESET
2010-05-18 07:45 . 2001-08-23 12:00 114176 —-a-w- c:windowssystem32qtdfysq.dll
2010-05-09 15:10 . 2010-05-09 15:10 ——– d—–w- c:documents and settingsTusrisepApplication DataCyberLink
2010-05-09 14:54 . 2010-03-04 15:58 ——– d—–w- c:documents and settingsTusrisepApplication DataAhead
2010-05-07 20:03 . 2010-05-07 20:03 22448 —-a-w- c:windowssystem32asr_05778.exe
2010-05-06 18:50 . 2010-05-06 18:50 ——– d—–w- c:documents and settingsAll UsersApplication DataSimply Super Software
2010-05-06 17:43 . 2010-03-04 12:22 ——– d—–w- c:program filesCamfrog
2010-04-19 16:12 . 2004-08-03 15:14 212736 —-a-w- c:windowssystem32driversndis.sys
2010-04-19 16:10 . 2004-08-03 16:56 14336 —-a-w- c:windowssystem32svchost.exe
2010-04-16 14:50 . 2010-04-16 14:46 44256 —-a-w- c:windowssystem32asr_14711.exe
2010-04-14 05:51 . 2010-04-14 05:51 1295744 —-a-w- c:windowssystem32PhotoJoy Screensaver.scr
2010-03-29 10:13 . 2010-03-29 10:13 95872 —-a-w- c:windowssystem32driversepfwtdir.sys
2010-03-29 10:12 . 2010-03-29 10:12 114984 —-a-w- c:windowssystem32driversehdrv.sys
2010-03-29 10:07 . 2010-03-29 10:07 140216 —-a-w- c:windowssystem32driverseamon.sys
2004-08-03 16:56 . 2004-08-03 16:56 165165 –sha-r- c:windowssystem32ivticrv.dll
.
——- Sigcheck ——-
[-] 2010-04-19 16:12 . 558635D3AF1C7546D26067D5D9B6959E . 212736 . . [——] . . c:windowssystem32driversndis.sys
[7] 2004-08-03 . 9F4B36614A0FC234525BA224957DE55C . 359040 . . [5.1.2600.2180] . . c:windowssystem32dllcachetcpip.sys
[-] 2004-08-03 . 7399D854596BFEFEED6B60879F28CE07 . 359040 . . [5.1.2600.2180] . . c:windowssystem32driverstcpip.sys
.
((((((((((((((((((((((((((((((((((((( Reg Loading Points ))))))))))))))))))))))))))))))))))))))))))))))))))
.
.
*Note* empty entries & legit default entries are not shown
REGEDIT4
[HKEY_CURRENT_USERSoftwareMicrosoftInternet ExplorerURLSearchHooks]
“{00000000-6E41-4FD3-8538-502F5495E5FC}”= “c:program filesAsk.comGenericAskToolbar.dll” [2010-05-26 1385864]
[HKEY_CLASSES_ROOTclsid{00000000-6e41-4fd3-8538-502f5495e5fc}]
[HKEY_LOCAL_MACHINE~Browser Helper Objects{D4027C7F-154A-4066-A1AD-4243D8127440}]
2010-05-26 08:23 1385864 —-a-w- c:program filesAsk.comGenericAskToolbar.dll
[HKEY_LOCAL_MACHINESOFTWAREMicrosoftInternet ExplorerToolbar]
“{D4027C7F-154A-4066-A1AD-4243D8127440}”= “c:program filesAsk.comGenericAskToolbar.dll” [2010-05-26 1385864]
[HKEY_CLASSES_ROOTclsid{d4027c7f-154a-4066-a1ad-4243d8127440}]
[HKEY_CLASSES_ROOTGenericAskToolbar.ToolbarWnd.1]
[HKEY_CLASSES_ROOTTypeLib{2996F0E7-292B-4CAE-893F-47B8B1C05B56}]
[HKEY_CLASSES_ROOTGenericAskToolbar.ToolbarWnd]
[HKEY_CURRENT_USERSoftwareMicrosoftInternet ExplorerToolbarWebbrowser]
“{D4027C7F-154A-4066-A1AD-4243D8127440}”= “c:program filesAsk.comGenericAskToolbar.dll” [2010-05-26 1385864]
[HKEY_CLASSES_ROOTclsid{d4027c7f-154a-4066-a1ad-4243d8127440}]
[HKEY_CLASSES_ROOTGenericAskToolbar.ToolbarWnd.1]
[HKEY_CLASSES_ROOTTypeLib{2996F0E7-292B-4CAE-893F-47B8B1C05B56}]
[HKEY_CLASSES_ROOTGenericAskToolbar.ToolbarWnd]
[HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionRun]
“SM?RT-Protection”=”c:program filesSmadavSM?RTP.exe” [?]
“VTTimer”=”VTTimer.exe” [2007-12-20 77824]
“S3Trayp”=”S3trayp.exe” [2007-09-30 200704]
“TrojanScanner”=”c:program filesTrojan RemoverTrjscan.exe” [2010-02-27 1165192]
“egui”=”c:program filesESETESET NOD32 Antivirusegui.exe” [2010-03-29 2145000]
[HKLM~startupfolderC:^Documents and Settings^All Users^Start Menu^Programs^Startup^Adobe Gamma Loader.lnk]
path=c:documents and settingsAll UsersStart MenuProgramsStartupAdobe Gamma Loader.lnk
backup=c:windowspssAdobe Gamma Loader.lnkCommon Startup
[HKLM~startupfolderC:^Documents and Settings^All Users^Start Menu^Programs^Startup^HotKeyDriver.lnk]
path=c:documents and settingsAll UsersStart MenuProgramsStartupHotKeyDriver.lnk
backup=c:windowspssHotKeyDriver.lnkCommon Startup
[HKLM~startupfolderC:^Documents and Settings^Tusrisep^Start Menu^Programs^Startup^OneNote 2007 Screen Clipper and Launcher.lnk]
path=c:documents and settingsTusrisepStart MenuProgramsStartupOneNote 2007 Screen Clipper and Launcher.lnk
backup=c:windowspssOneNote 2007 Screen Clipper and Launcher.lnkStartup
[HKEY_LOCAL_MACHINEsoftwaremicrosoftshared toolsmsconfigstartupregMSConfig]
c:documents and settingsTusrisepsxja.exe u [X]
[HKEY_LOCAL_MACHINEsoftwaremicrosoftshared toolsmsconfigstartupregAdobe Reader Speed Launcher]
2009-02-27 10:10 35696 —-a-w- c:program filesAdobeReader 9.0Readerreader_sl.exe
[HKEY_LOCAL_MACHINEsoftwaremicrosoftshared toolsmsconfigstartupregAnti Trojan Elite]
2009-06-13 19:48 4076544 —-a-w- c:program filesAnti Trojan EliteTJEnder.exe
[HKEY_LOCAL_MACHINEsoftwaremicrosoftshared toolsmsconfigstartupregBgMonitor_{79662E04-7C6C-4d9f-84C7-88D8A56B10AA}]
2006-12-23 11:05 143360 —-a-w- c:program filesCommon FilesAheadLibNMBgMonitor.exe
[HKEY_LOCAL_MACHINEsoftwaremicrosoftshared toolsmsconfigstartupregBisonHK]
2008-03-25 08:46 77824 —-a-w- c:windowsBisonCamBisonHK.exe
[HKEY_LOCAL_MACHINEsoftwaremicrosoftshared toolsmsconfigstartupregconime.exe]
2004-08-03 16:56 27648 —-a-w- c:windowssystem32conime.exe
[HKEY_LOCAL_MACHINEsoftwaremicrosoftshared toolsmsconfigstartupregctfmon.exe]
2004-08-03 16:56 15360 —-a-w- c:windowssystem32ctfmon.exe
[HKEY_LOCAL_MACHINEsoftwaremicrosoftshared toolsmsconfigstartupregGrooveMonitor]
2006-10-26 17:47 31016 —-a-w- c:program filesMicrosoft OfficeOffice12GrooveMonitor.exe
[HKEY_LOCAL_MACHINEsoftwaremicrosoftshared toolsmsconfigstartupregHDAudDeck]
2007-10-12 06:16 794624 —-a-r- c:program filesVIAVIAudioiHDADeckHDeck.exe
[HKEY_LOCAL_MACHINEsoftwaremicrosoftshared toolsmsconfigstartupregLanguageShortcut]
2006-12-05 15:55 54832 —-a-w- c:program filesCyberLinkPowerDVDLanguageLanguage.exe
[HKEY_LOCAL_MACHINEsoftwaremicrosoftshared toolsmsconfigstartupregMessenger (Yahoo!)]
2009-11-10 08:39 5244216 —-a-w- c:program filesYahoo!MessengerYahooMessenger.exe
[HKEY_LOCAL_MACHINEsoftwaremicrosoftshared toolsmsconfigstartupregNeroFilterCheck]
2006-01-12 08:40 155648 —-a-w- c:program filesCommon FilesAheadLibNeroCheck.exe
[HKEY_LOCAL_MACHINEsoftwaremicrosoftshared toolsmsconfigstartupregPhotoJoy]
2010-04-14 05:52 972160 —-a-w- c:program filesPhotoJoyBinPhotoJoy.exe
[HKEY_LOCAL_MACHINEsoftwaremicrosoftshared toolsmsconfigstartupregRemoteControl]
2006-11-23 08:10 56928 ——w- c:program filesCyberLinkPowerDVDPDVDServ.exe
[HKEY_LOCAL_MACHINEsoftwaremicrosoftshared toolsmsconfigstartupregSMSERIAL]
2007-01-17 21:34 634880 —-a-r- c:program filesMotorolaSMSERIALsm56hlpr.exe
[HKEY_LOCAL_MACHINEsoftwaremicrosoftshared toolsmsconfigstartupregSunJavaUpdateSched]
2009-10-10 21:17 149280 —-a-w- c:program filesJavajre6binjusched.exe
[HKEY_LOCAL_MACHINEsoftwaremicrosoftshared toolsmsconfigstartupregSynTPStart]
2007-08-17 06:40 102400 —-a-w- c:program filesSynapticsSynTPSynTPStart.exe
[HKEY_LOCAL_MACHINEsoftwaremicrosoftsecurity center]
“AntiVirusOverride”=dword:00000001
“FirewallOverride”=dword:00000001
[HKLM~servicessharedaccessparametersfirewallpolicystandardprofile]
“EnableFirewall”= 0 (0x0)
[HKLM~servicessharedaccessparametersfirewallpolicystandardprofileAuthorizedApplicationsList]
“%windir%system32sessmgr.exe”=
R1 ehdrv;ehdrv;c:windowssystem32driversehdrv.sys [3/29/2010 5:12 PM 114984]
R1 epfwtdir;epfwtdir;c:windowssystem32driversepfwtdir.sys [3/29/2010 5:13 PM 95872]
R2 ekrn;ESET Service;c:program filesESETESET NOD32 Antivirusekrn.exe [3/29/2010 5:12 PM 810120]
R3 RTLWUSB;Realtek RTL8187 Wireless 802.11g 54Mbps USB 2.0 Network Adapter;c:windowssystem32driversRTL8187.sys [3/4/2010 10:12 PM 180480]
R3 VIAHdAudAddService;VIA High Definition Audio Driver Service;c:windowssystem32driversviahduaa.sys [3/4/2010 10:05 PM 205184]
S0 vfxhrpss;vfxhrpss; [x]
S2 ATE_PROCMON;ATE_PROCMON;??c:program filesAnti Trojan EliteATEPMon.sys –> c:program filesAnti Trojan EliteATEPMon.sys [?]
S2 dtlynscl;Keyboard Class Helper;c:windowsSystem32svchost.exe -k netsvcs [8/3/2004 11:56 PM 14336]
S2 kjoenp;kjoenp;c:windowssystem32svchost.exe -k netsvcs [8/3/2004 11:56 PM 14336]
S2 nwjoml;nwjoml;c:windowssystem32svchost.exe -k netsvcs [8/3/2004 11:56 PM 14336]
S2 obsjghqbx;obsjghqbx;c:windowssystem32svchost.exe -k netsvcs [8/3/2004 11:56 PM 14336]
S3 ManyCam;ManyCam Virtual Webcam, WDM Video Capture Driver;c:windowssystem32DRIVERSManyCam.sys –> c:windowssystem32DRIVERSManyCam.sys [?]
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindows NTCurrentVersionSvchost – NetSvcs
dtlynscl
ricdcz
azsynxv
nfhmnlgrn
nwjoml
kjoenp
obsjghqbx
.
Contents of the ‘Scheduled Tasks’ folder
2010-06-14 c:windowsTasksScheduled Update for Ask Toolbar.job
– c:program filesAsk.comUpdateTask.exe [2010-05-26 08:23]
.
.
——- Supplementary Scan ——-
.
uStart Page = hxxp://www.google.co.id/
IE: E&xport to Microsoft Excel – c:progra~1MICROS~2Office12EXCEL.EXE/3000
FF – ProfilePath – c:documents and settingsTusrisepApplication DataMozillaFirefoxProfilesc2t8bt4k.default
FF – prefs.js: browser.search.selectedEngine – Ask.com
FF – prefs.js: browser.startup.homepage – hxxp://www.google.co.id/
FF – prefs.js: keyword.URL – hxxp://websearch.ask.com/redirect?client=ff&src=kw&tb=CS2&o=15673&locale=en_US&apn_uid=DE2E6760-3A55-476C-A626-D96328F00A09&apn_ptnrs=HL&apn_sauid=DF33C787-8D15-47B4-9529-630EBBDC094A&apn_dtid=&q=
FF – prefs.js: network.proxy.type – 4
—- FIREFOX POLICIES —-
c:program filesMozilla Firefox 3.6 Beta 5greprefsall.js – pref(“ui.use_native_colors”, true);
c:program filesMozilla Firefox 3.6 Beta 5greprefsall.js – pref(“network.auth.force-generic-ntlm”, false);
c:program filesMozilla Firefox 3.6 Beta 5greprefsall.js – pref(“network.proxy.type”, 5);
c:program filesMozilla Firefox 3.6 Beta 5greprefsall.js – pref(“dom.ipc.plugins.timeoutSecs”, 10);
c:program filesMozilla Firefox 3.6 Beta 5greprefsall.js – pref(“svg.smil.enabled”, false);
c:program filesMozilla Firefox 3.6 Beta 5greprefsall.js – pref(“accelerometer.enabled”, true);
c:program filesMozilla Firefox 3.6 Beta 5greprefssecurity-prefs.js – pref(“security.ssl.allow_unrestricted_renego_everywhere__temporarily_available_pref”, true);
c:program filesMozilla Firefox 3.6 Beta 5greprefssecurity-prefs.js – pref(“security.ssl.renego_unrestricted_hosts”, “”);
c:program filesMozilla Firefox 3.6 Beta 5greprefssecurity-prefs.js – pref(“security.ssl.treat_unsafe_negotiation_as_broken”, false);
c:program filesMozilla Firefox 3.6 Beta 5greprefssecurity-prefs.js – pref(“security.ssl.require_safe_negotiation”, false);
c:program filesMozilla Firefox 3.6 Beta 5defaultspreffirefox.js – pref(“extensions.{972ce4c6-7e08-4474-a285-3208198ce6fd}.name”, “chrome://browser/locale/browser.properties”);
c:program filesMozilla Firefox 3.6 Beta 5defaultspreffirefox.js – pref(“extensions.{972ce4c6-7e08-4474-a285-3208198ce6fd}.description”, “chrome://browser/locale/browser.properties”);
c:program filesMozilla Firefox 3.6 Beta 5defaultspreffirefox.js – pref(“plugins.update.notifyUser”, false);
c:program filesMozilla Firefox 3.6 Beta 5defaultspreffirefox.js – pref(“dom.ipc.plugins.enabled.nptest.dll”, true);
c:program filesMozilla Firefox 3.6 Beta 5defaultspreffirefox.js – pref(“dom.ipc.plugins.enabled.npswf32.dll”, true);
c:program filesMozilla Firefox 3.6 Beta 5defaultspreffirefox.js – pref(“dom.ipc.plugins.enabled.npctrl.dll”, true);
c:program filesMozilla Firefox 3.6 Beta 5defaultspreffirefox.js – pref(“dom.ipc.plugins.enabled.npqtplugin.dll”, true);
c:program filesMozilla Firefox 3.6 Beta 5defaultspreffirefox.js – pref(“dom.ipc.plugins.enabled”, false);
.
– – – – ORPHANS REMOVED – – – –
MSConfigStartUp-Camfrog – c:program filesCamfrogCamfrog Video ChatCamfrogNet.exe
MSConfigStartUp-games – c:recyclerS-1-5-21-0243556031-888888379-781863308-1451games.exe
MSConfigStartUp-Google Update – c:documents and settingsTusrisepLocal SettingsApplication DataGoogleUpdateGoogleUpdate.exe
MSConfigStartUp-guefae – c:documents and settingsTusrisepguefae.exe
MSConfigStartUp-TE_RegProtect – c:program filesAnti Trojan EliteTERegPct.exe
**************************************************************************
catchme 0.3.1398 W2K/XP/Vista – rootkit/stealth malware detector by Gmer, http://www.gmer.net
Rootkit scan 2010-06-15 01:03
Windows 5.1.2600 Service Pack 2 NTFS
scanning hidden processes …
scanning hidden autostart entries …
scanning hidden files …
scan completed successfully
hidden files: 0
**************************************************************************
Stealth MBR rootkit/Mebroot/Sinowal detector 0.3.7 by Gmer, http://www.gmer.net
device: opened successfully
user: MBR read successfully
called modules: ntkrnlpa.exe >>UNKNOWN [0x858F1580]<<
kernel: MBR read successfully
detected MBR rootkit hooks:
DriverDisk -> CLASSPNP.SYS @ 0xf75b6fc3
DriverACPI -> ACPI.sys @ 0xf7449cb8
Driveratapi -> atapi.sys @ 0xf73db7b4
IoDeviceObjectType -> DeleteProcedure -> ntkrnlpa.exe @ 0x8058236c
ParseProcedure -> ntkrnlpa.exe @ 0x8058146a
DeviceHarddisk0DR0 -> DeleteProcedure -> ntkrnlpa.exe @ 0x8058236c
ParseProcedure -> ntkrnlpa.exe @ 0x8058146a
NDIS: -> SendCompleteHandler -> 0x0
PacketIndicateHandler -> 0x0
SendHandler -> 0x0
user & kernel MBR OK
**************************************************************************
.
——————— DLLs Loaded Under Running Processes ———————
– – – – – – – > ‘explorer.exe'(3920)
c:windowssystem32hnetcfg.dll
.
———————— Other Running Processes ————————
.
c:program filesJavajre6binjqs.exe
c:program filesCyberLinkShared FilesRichVideo.exe
c:windowssystem32wdfmgr.exe
c:windowssystem32VTTimer.exe
c:windowssystem32S3trayp.exe
.
**************************************************************************
.
Completion time: 2010-06-15 01:07:37 – machine was rebooted
ComboFix-quarantined-files.txt 2010-06-14 18:07
Pre-Run: 23,312,326,656 bytes free
Post-Run: 23,435,890,688 bytes free
WindowsXP-KB310994-SP2-Pro-BootDisk-ENU.exe
[boot loader]
timeout=2
default=multi(0)disk(0)rdisk(0)partition(1)WINDOWS
[operating systems]
c:cmdconsBOOTSECT.DAT=”Microsoft Windows Recovery Console” /cmdcons
multi(0)disk(0)rdisk(0)partition(1)WINDOWS=”Microsoft Windows XP Professional” /noexecute=optin /fastdetect
– – End Of File – – 114169F60A91B3458F4401EFC8E17F06
Dari Berbagai Sumber.







